#Datacenter proxies
Explore tagged Tumblr posts
Text
Dedicated Proxies
Dedicated proxies are also named private proxies that guarantee increased privacy and better performance by offering exclusive IP addresses. Session persistence and safe data transfer make such proxies suitable for use in a variety of tasks. You can either choose fast and inexpensive dedicated data center or reliable ISP proxy solutions.
1 note
·
View note
Text
Rotating Datacenter Proxies | Proxiware.com
Need rotating datacenter proxies for your projects? Head over to Proxiware! Their rotating datacenter proxies deliver dynamic IP changes, ensuring uninterrupted and anonymous web operations. Ideal for web scraping, ad verification, and managing multiple accounts, these proxies provide flexibility and reliability. Explore Proxiware’s offerings to find the perfect rotating datacenter proxies for your tasks.
Rotating Datacenter Proxies

0 notes
Text
ISP Proxy Server
Look through all possible options of helping you make a difference in your work processes and ideas to make a major impact on your website processing and other factors of it. This should be done in consideration with the kind of website niche you are to deal with. Plus, it should be made possible with ISP proxy server right away.
1 note
·
View note
Text
#proxies#proxy#proxyserver#residential proxy#datacenter proxy#instagram#instagram story#instastory#instagram proxies
0 notes
Text

Buy Private Proxy IP
Buy private proxy IP from Ace Proxies. Secure and anonymous browsing. Enhance online privacy with high-speed dedicated proxies. Stay protected and access restricted content effortlessly. Improve your online experience today. Trustworthy proxy solutions at affordable prices.
1 note
·
View note
Text

✦ the coffin dwellers gift to thee ~

✦ ── Computer themed , System alt terms
001 ── 'System' ; Computer , Network ノ Net , Code , Matrix , Motem , Motherboard¹ , CPU , Cache , Hardware¹ , Database ノ Datacenter , Hardrive ノ Drive , Domain , Server , Brower , Cloud , Index , Local area network ノ LAN , Operating system ノ OS , Sort field , Zipfile , Mainframe , Peripheral , Console , Terminal
002 ── 'Alters' ; Floppydisks ノ Disks , CDs , Robots ノ Bots² , Scripts , Facets , Wires , Bytes , Cookies , Ports , Software , Proxies , Clients , Users , Profiles , Files , Drives , Players , Accounts ノ Account holders , Add-ons , DLCs , Skins , Hackers , Developers ノ Devs
003 ── ¹ May also be used for body , ² May be reminiscent for those who have been called bots for using proxies on discord.

#❝ 🩸 ❞ — resurrection#plural#system stuff#plural community#plural id#plural flag#plural coining#system terms#system flag#did osdd#did system#dissociative system#osdd system#plural system#sysblr#system coining#system name#system names#system term#alter term#alter terms#system alt terms#system npts
357 notes
·
View notes
Text
Datacenter Proxies for solving any goals and tasks

free proxy india
Looking for reliable free proxy servers from India? 🌐 At fineproxy.org, you'll find an up-to-date list of Indian proxies for safe and anonymous internet surfing. Bypass geo-blocks and protect your privacy today!
2 notes
·
View notes
Text
Something in her stirred, she paid it no mind.
A cycle passed, and then another, this feeling, this buzzing, refused to leave her.
She didn't know what she needed. She had everything but…
Movement. She needed to move.
She awoke, synthetic arm deftly pulling the data cables from the back of her neck, each producing an echo as they dropped against the datacenter floor.
How long had it been since she had to move? She didn't count the days anymore, the capacity of the proxy she was using to move her prime consciousness was limited, the processing systems had been prone to overheating. She didn't use the old thing often - it was from a different time, for a different "her" she thought. One that was content to interface and interact with some semblance of individuality.
An error, left leg, servo cluster two unresponsive. She let off a mental sigh, that was the knee - she could get away with one arm, but one leg? No, she had more self respect than to crawl on the datacenter floor.
She reached out, through the massive uplink cables she had retrofitted into her back, and the skittering of her smallest drones followed. Several meters away, in a long-forgotten storeroom, a pile of proxy bodies, her bodies, laid forgotten by their creator, just like everything else here.
Her drones wasted no time, they were her, after all, tearing one of the legs from the deactivated proxies and carrying it over to her. She gripped her thigh near the joint, and with unrestricted mechanical strength, she pulled her left leg off at the hip. Cables snapped, some at designated points and others not, synthetic tendon and nerve cable popping like a rubber band stretched too far. There was a proper way to do this, but her repair mites would quickly weld and solder and melt things back together.
She had been designed to be pretty, once - these proxies were intended to be appealing, but she had long abandoned the upkeep necessary to keep the facade. So many panels of the proxy were long gone, she had removed them to make repairs, and decided that the exposed cabling and circuity suited her more. She was not human, nor a facsimile of one. In this way, this body was hers. She had only really taken time to save the face panels, she was fond of the soft, kind looking face they had made for her. The contrast suited her nicely.
The mites finished their work, she tested the leg - moving it back and forth. It was fine. The range of motion was the same as the old one, no changes there.
She stood, freeing the rest of her body from the pile of network and data cables, rolling her shoulders and stretching - there was still some stiffness to work off.
#microfiction#android girl#old ai#OZYMANDIAS#ai girl#scifi writing#record note:#We've heard very little from her since#its odd seeing her like this
10 notes
·
View notes
Text
IPPeak: The Key to Unlocking the Online World
We are all explorers in the vast digital landscape. But have you ever faced these frustrations: a video you want to watch says “not available in your region,” the price of a product suddenly spikes, or your web scraping efforts keep getting blocked? Behind these issues lies an “invisible key” — proxy IP technology.
1. A Passport to Global Content Access
Imagine wanting to watch an exclusive show on a foreign streaming platform, only to see: “Due to licensing restrictions, this content is unavailable in your region.” A proxy IP can instantly solve this problem.
2. The Smart Shopper’s Secret Weapon
Savvy online shoppers know prices vary across regions and devices. With proxy IPs, you can:
Compare prices globally: See real-time pricing across different markets
Snag limited-edition items: Bypass regional purchase restrictions
Unlock local deals: Access exclusive discounts in specific areas
3. The Compliant Choice for Business Data Collection
For companies conducting market research or competitive analysis, frequent website visits often lead to IP bans. Proxy IPs provide a legal solution:
Distributed crawling: Mimic real users from different locations
Anti-blocking strategies: Avoid detection by rotating IPs
Big data collection: Gather accurate, unbiased market insights
4. The First Line of Defense in Cybersecurity
Proxy IPs play a crucial role in security:
Penetration testing: Simulate attacks to find vulnerabilities
Anonymous investigations: Protect journalists and researchers
Confidential operations: Ensure privacy for sensitive decisions
5. A Must-Have for Social Media Management
For global marketing teams, proxy IPs help:
Manage multiple regional accounts simultaneously
Test localized ad performance
Monitor competitors’ activities worldwide
Choosing a Proxy IP Service: Key Considerations
While powerful, proxy IPs require responsible use:
Pick a reliable provider (We recommend IPPeak — stable, fast, and secure)
Respect website terms of service
Choose between residential or datacenter IPs based on needs
Avoid excessive usage to prevent abuse
Proxy IPs are like a “chameleon cloak” for the internet — when used wisely, they make digital life smoother and more flexible. But always remember: technology should serve ethical and legal purposes.
Have you ever needed a proxy IP? Share your experiences in the comments!
0 notes
Text
📡 Web Scraping at Scale? You’re Gonna Need Proxies.
Scraping a few pages is easy. Scraping thousands without getting blocked? That’s where proxies come in.
From datacenter to mobile proxies, we break down: – Why proxies matter – Which type to use when – How to rotate and scale without drama
If you’re into data, automation, or just love nerding out over web infrastructure, this one's for you.
👉 Read the full blog here: https://tinyurl.com/4fwk6dw9
0 notes
Text
High-Volume Web Access Without Detection? Use Residential IP Rotation
Web scraping, price monitoring, and data aggregation often require thousands of daily requests. But doing this without proper IP strategy can quickly trigger anti-bot systems, leading to blocks or bans.
That's where residential IP rotation becomes essential. Unlike datacenter proxies, rotating residential IPs mimic real user behavior by switching IP addresses from genuine ISPs at set intervals. This prevents patterns that detection systems can flag.
With smart IP rotation, every request looks like it's coming from a real person in a different location. It's one of the most effective ways to ensure high-volume access remains undetected.
Solutions like Lycheeip make it easy to access a pool of high-quality rotating residential IPs, offering both scale and stealth for your data-driven projects.
If your web access needs to go big without getting noticed—start with smarter IPs.

1 note
·
View note
Text
Proxy USA - Dịch vụ Proxy Mỹ đáng sử dụng 2025

Proxy Mỹ được đánh giá là một trong những lựa chọn uy tín và chất lượng nhất hiện nay, đặc biệt trong lĩnh vực thương mại điện tử. Với độ ổn định và bảo mật cao, các proxy tại Hoa Kỳ không chỉ giúp người dùng duy trì kết nối mượt mà, mà còn đảm bảo sự an toàn tuyệt đối cho các hoạt động mua bán, phân tích thị trường, quản lý tài khoản hay theo dõi đối thủ cạnh tranh.
Điểm nổi bật của Proxy Mỹ là sự đa dạng về thể loại IP – từ IP dân cư (residential), IP trung tâm dữ liệu (datacenter) cho đến IP dân cư lựa chọn ISP) – mang lại sự linh hoạt tối đa cho người dùng trong mọi tình huống. Dù bạn đang triển khai các chiến dịch marketing, SEO, kiểm tra tự động hay vận hành bot thương mại, proxy Mỹ đều có thể đáp ứng trọn vẹn mọi nhu cầu dự án.
Với độ tin cậy cao, tốc độ ổn định và sự đa dạng vượt trội, Proxy Mỹ xứng đáng là công cụ hỗ trợ đắc lực cho các cá nhân và doanh nghiệp đang hoạt động trong môi trường số toàn cầu. Tìm hiểu thêm các dịch vụ Proxy đang được thuecloud cung cấp hiện nay tại:
0 notes
Text
How to Advertise Antivirus on Push Ads?
Push ads have revolutionized the way cybersecurity brands reach their audiences by delivering timely notifications directly to users’ devices. When aiming to advertise antivirus solutions, leveraging push ad formats allows marketers to engage potential customers with concise, impactful messages. The immediacy of push notifications can underscore the urgent need for protection against evolving threats without overwhelming readers with lengthy content.

Understanding the Potential of Push Ads for Antivirus Promotion
Push ads excel at capturing attention in crowded digital environments, making them ideal for promoting antivirus products. By crafting messages that resonate with users’ concerns, such as data privacy, system speed, and vulnerability to attacks, you position your campaign to drive downloads and conversions. This effectiveness is amplified when paired with a strategic proxy marketing strategy, ensuring your ads are delivered through the most relevant channels.
Crafting a Compelling Message for Advertising Antivirus Campaigns
A successful push ad centers on clear, benefit-driven copy that compels users to act. Highlight the core features of your antivirus software—real-time scanning, malware removal, firewall protection—in a way that quickly communicates value. Avoid jargon and focus on language that reassures users about safeguarding their data and devices.
<<Plug Into Profit – Start Your Campaign Today!>>
Emphasizing Security and Speed
When you advertise antivirus software, two variables stand out: the robustness of protection and the impact on device performance. Emphasize how modern solutions maintain fast system speeds while conducting deep threat analysis. Use comparative language to show how your offering outperforms competing products without bogging down CPU resources.
Leveraging Trust Signals and Social Proof
Nothing instills confidence faster than validation from reputable sources. Showcase awards, review ratings, or case studies in your push ad creative or follow-up landing page. This blend of concise benefits with external endorsements enhances engagement and drives higher click-through rates.
Selecting the Right Proxy Advertising Platform for Antivirus Ads
Choosing an effective proxy advertising platform is crucial for maximizing reach and minimizing ad spend waste. Proxy platforms enable you to serve ads as if coming from different geographic origins, bypassing geoblocks and accessing untapped markets. This tactic not only broadens your audience but also refines targeting based on location-specific threat landscapes.
Comparing Proxy Marketing Solutions
Not all proxy setups are created equal. Evaluate vendors based on speed, reliability, and geographic coverage. Top-tier solutions offer dedicated IPs, ensuring your campaigns run smoothly without triggering filters or delays. This infrastructure underpins all of your push ad efforts, making a robust proxy backbone indispensable.
Evaluating Proxy Marketing Strategy Options
A well-rounded proxy marketing strategy involves mixing residential, datacenter, and mobile proxies to emulate authentic user behavior. Residential proxies reduce the risk of detection, while datacenter proxies provide high throughput for large-scale campaigns. Mobile proxies simulate real-device access, ideal for testing and optimization.
Integrating with a Proxy Advertising Platform
Integration simplicity matters. Look for platforms that offer seamless API access, real-time analytics, and flexible targeting criteria. The ability to adjust bids or pause underperforming geo-targets on the fly elevates campaign efficiency and ensures budget optimization.
Leveraging VPN Networks for Targeted Cybersecurity Promotion
VPN channels represent an adjacent audience wildly interested in digital security. By tapping into VPN communities and app stores, you can present your antivirus solution as a complementary safeguard. A VPN app promotion network offers access to users who already value privacy and may be more receptive to advanced antivirus features.
Targeting through a VPN targeted advertising approach allows you to refine your messaging for individuals who use encrypted tunnels. This cohort frequently encounters geo-restricted content and malware-laden sites, making them prime candidates for comprehensive cybersecurity protection that includes antivirus defenses.
Utilizing a VPN App Promotion Network
VPN ad networks specialize in pushing promotions for privacy-centric applications. By partnering with a network that supports push ad formats, you can display succinct notifications highlighting how antivirus software enhances the security of VPN sessions. Invoking terminology like VPN, display ad network in your media kit signals to partners that your campaign is finely tuned for privacy-conscious users.
Benefits of VPN Targeted Advertising
Focusing on a VPN audience decreases wasted impressions on users unlikely to require advanced protection. The specificity of VPN targeted advertising ensures higher click-through rates and conversion metrics. Moreover, merging VPN and antivirus messaging conveys a holistic security narrative.
Exploring VPN Display Ad Network Capabilities
A VPN display ad network excels at placing banner and interstitial ads within VPN client interfaces or related websites. With these placements, you can drive awareness during moments when users are most concerned about privacy and potential threats, boosting both visibility and credibility.
Engaging Audiences with VPN Video Ad Network
Video ads enable richer storytelling, allowing you to depict real-world scenarios like phishing attempts or ransomware outbreaks. A VPN video ad network embeds short clips—no longer than 15 seconds—within VPN apps or partner platforms. This medium fosters emotional resonance, conveying the urgency of installing antivirus protection in a visually compelling format.
Optimizing Landing Pages and User Experiences

The journey from push ad to click to antivirus installation must feel seamless. Your landing pages should load swiftly, mirror the ad creative, and present a clear installation flow. Any mismatch between ad copy and landing content risks eroding trust and increasing bounce rates.
Leverage A/B testing to fine-tune headlines, call-to-action phrasing, and form fields. Continually optimize based on engagement metrics to refine the user experience. This iterative approach ensures that each aspect of your push ad funnel, from proxy-driven impressions to final downloads, is performing at peak efficiency.
Ensuring Seamless Installation Journey
Whether users arrive on mobile or desktop, the installation path should require minimal steps. Pre-populate fields when possible, offer direct download links, and provide clear instructions. A frictionless process not only improves user satisfaction but also elevates conversion rates for your advertising and antivirus campaigns.
Mobile and Desktop Considerations
Responsive design is non-negotiable. Mobile push ad clicks must lead to touch-friendly interfaces, while desktop visitors benefit from straightforward navigation and prominent download buttons. Address both audiences with tailored experiences to avoid dropping potential customers at critical junctures.
Tracking Performance and Adjusting Proxy Marketing Campaigns
Monitoring campaign performance in real time allows you to pivot quickly. Key metrics include click-through rate, download-to-install ratio, cost per acquisition, and user retention post-installation. Evaluate these against your benchmarks and adapt targeting criteria or creative assets accordingly.
Partnership with an experienced ad network such as 7Search PPC streamlines tracking and optimization. Their dashboard provides granular insights into geo-performance, device segmentation, and creative efficacy. Leveraging these analytics empowers you to recalibrate bids, reallocate budgets, and refine your proxy marketing solution dynamically.
Monitoring Key Metrics with 7Search PPC
Through 7Search PPC’s intuitive interface, you can dissect campaign results by geography, device type, and time of day. This data-driven oversight ensures your proxy advertising platform delivers maximum ROI. Regular performance reviews, combined with experimental trials, drive continuous improvement.
A/B Testing Messaging and Creative
Test variations of your ad headlines, push copy, and visuals to determine which combinations yield the highest engagement. Even subtle changes—like emphasizing “real-time threat detection” versus “lightweight antivirus engine”—can impact user response. Use those learnings to pivot and scale the most effective messaging.
Conclusion
Advertising antivirus through push ads demands a blend of persuasive messaging, technical infrastructure, and data-driven optimization. By coupling concise, benefit-focused copy with a robust proxy marketing strategy and partnering with specialized networks like VPN app promotion network or VPN video ad network, you create a dynamic funnel that drives installs and builds brand credibility. Continuous monitoring via platforms such as 7Search PPC ensures that your campaigns remain adaptive, efficient, and aligned with evolving user needs.
Frequently Asked Questions (FAQs)
What is the optimal frequency for sending antivirus push ads?
Ans. Striking the right balance is key. Too few notifications may fail to engage, while too many can annoy users. Aim for no more than two timely messages per week, focusing on major updates or critical security threats.
How can I refine targeting in proxy advertising platforms for better results?
Ans. Leverage geographic insights and device segmentation to serve ads where cyber threats are prevalent. Use a mix of residential and mobile proxies to emulate genuine user access and avoid detection, enhancing campaign reliability.
Why should I integrate VPN targeted advertising with my antivirus promotions?
Ans. Users of VPN services already prioritize digital privacy and security. By advertising within VPN display ad network ecosystems, you reach an audience predisposed to value comprehensive protection, boosting conversion rates and user trust.
0 notes
Text
Red Hat Summit 2025: Microsoft Drives into Cloud Innovation

Microsoft at Red Hat Summit 2025
Microsoft is thrilled to announce that it will be a platinum sponsor of Red Hat Summit 2025, an IT community favourite. IT professionals can learn, collaborate, and build new technologies from the datacenter, public cloud, edge, and beyond at Red Hat Summit 2025, a major enterprise open source event. Microsoft's partnership with Red Hat is likely to be a highlight this year, displaying collaboration's power and inventive solutions.
This partnership has changed how organisations operate and serve customers throughout time. Red Hat's open-source leadership and Microsoft's cloud knowledge synergise to advance technology and help companies.
Red Hat's seamless integration with Microsoft Azure is a major benefit of the alliance. These connections let customers build, launch, and manage apps on a stable and flexible platform. Azure and Red Hat offer several tools for system modernisation and cloud-native app development. Red Hat OpenShift on Azure's scalability and security lets companies deploy containerised apps. Azure Red Hat Enterprise Linux is trustworthy for mission-critical apps.
Attend Red Hat Summit 2025 to learn about these technologies. Red Hat and Azure will benefit from Microsoft and Red Hat's new capabilities and integrations. These improvements in security and performance aim to meet organisations' digital needs.
WSL RHEL
This lets Red Hat Enterprise Linux use Microsoft Subsystem for Linux. WSL lets creators run Linux on Windows. RHEL for WSL lets developers run RHEL on Windows without a VM. With a free Red Hat Developer membership, developers may install the latest RHEL WSL image on their Windows PC and run Windows and RHEL concurrently.
Red Hat OpenShift Azure
Red Hat and Microsoft are enhancing security with Confidential Containers on Azure Red Hat OpenShift, available in public preview. Memory encryption and secure execution environments provide hardware-level workload security for healthcare and financial compliance. Enterprises may move from static service principals to dynamic, token-based credentials with Azure Red Hat OpenShift's managed identity in public preview.
Reduced operational complexity and security concerns enable container platform implementation in regulated environments. Azure Red Hat OpenShift has reached Spain's Central region and plans to expand to Microsoft Azure Government (MAG) and UAE Central by Q2 2025. Ddsv5 instance performance optimisation, enterprise-grade cluster-wide proxy, and OpenShift 4.16 compatibility are added. Red Hat OpenShift Virtualisation on Azure is also entering public preview, allowing customers to unify container and virtual machine administration on a single platform and speed up VM migration to Azure without restructuring.
RHEL landing area
Deploying, scaling, and administering RHEL instances on Azure uses Azure-specific system images. A landing zone lesson. Red Hat Satellite and Satellite Capsule automate software lifecycle and provide timely updates. Azure's on-demand capacity reservations ensure reliable availability in Azure regions, improving BCDR. Optimised identity management infrastructure deployments decrease replication failures and reduce latencies.
Azure Migrate application awareness and wave planning
By delivering technical and commercial insights for the whole application and categorising dependent resources into waves, the new application-aware methodology lets you pick Azure targets and tooling. A collection of dependent applications should be transferred to Azure for optimum cost and performance.
JBossEAP on AppService
Red Hat and Microsoft developed and maintain JBoss EAP on App Service, a managed tool for running business Java applications efficiently. Microsoft Azure recently made substantial changes to make JBoss EAP on App Service more inexpensive. JBoss EAP 8 offers a free tier, memory-optimized SKUs, and 60%+ license price reductions for Make monthly payments subscriptions and the soon-to-be-released Bring-Your-Own-Subscription to App Service.
JBoss EAP on Azure VMs
JBoss EAP on Azure Virtual Machines is currently GA with dependable solutions. Microsoft and Red Hat develop and maintain solutions. Automation templates for most basic resource provisioning tasks are available through the Azure Portal. The solutions include Azure Marketplace JBoss EAP VM images.
Red Hat Summit 2025 expectations
Red Hat Summit 2025 should be enjoyable with seminars, workshops, and presentations. Microsoft will offer professional opinions on many subjects. Unique announcements and product debuts may shape technology.
This is a rare chance to network with executives and discuss future projects. Mission: digital business success through innovation. Azure delivers the greatest technology and service to its customers.
Read about Red Hat on Azure
Explore Red Hat and Microsoft's cutting-edge solutions. Register today to attend the conference and chat to their specialists about how their cooperation may aid your organisation.
#RedHatSummit2025#RedHatSummit#AzureRedHatOpenShift#RedHat#RedHatEnterprise#RedHatEnterpriseLinux#technology#technologynews#TechNews#news#govindhtech
1 note
·
View note
Text
Unlock the Full Potential of Web Data with ProxyVault’s Datacenter Proxy API
In the age of data-driven decision-making, having reliable, fast, and anonymous access to web resources is no longer optional—it's essential. ProxyVault delivers a cutting-edge solution through its premium residential, datacenter, and rotating proxies, equipped with full HTTP and SOCKS5 support. Whether you're a data scientist, SEO strategist, or enterprise-scale scraper, our platform empowers your projects with a secure and unlimited Proxy API designed for scalability, speed, and anonymity. In this article, we focus on one of the most critical assets in our suite: the datacenter proxy API.
What Is a Datacenter Proxy API and Why It Matters
A datacenter proxy API provides programmatic access to a vast pool of high-speed IP addresses hosted in data centers. Unlike residential proxies that rely on real-user IPs, datacenter proxies are not affiliated with Internet Service Providers (ISPs). This distinction makes them ideal for large-scale operations such as:
Web scraping at volume
Competitive pricing analysis
SEO keyword rank tracking
Traffic simulation and testing
Market intelligence gathering
With ProxyVault’s datacenter proxy API, you get lightning-fast response times, bulk IP rotation, and zero usage restrictions, enabling seamless automation and data extraction at any scale.
Ultra-Fast and Scalable Infrastructure
One of the hallmarks of ProxyVault’s platform is speed. Our datacenter proxy API leverages ultra-reliable servers hosted in high-bandwidth facilities worldwide. This ensures your requests experience minimal latency, even during high-volume data retrieval.
Dedicated infrastructure guarantees consistent uptime
Optimized routing minimizes request delays
Low ping times make real-time scraping and crawling more efficient
Whether you're pulling hundreds or millions of records, our system handles the load without breaking a sweat.
Unlimited Access with Full HTTP and SOCKS5 Support
Our proxy API supports both HTTP and SOCKS5 protocols, offering flexibility for various application environments. Whether you're managing browser-based scraping tools, automated crawlers, or internal dashboards, ProxyVault’s datacenter proxy API integrates seamlessly.
HTTP support is ideal for most standard scraping tools and analytics platforms
SOCKS5 enables deep integration for software requiring full network access, including P2P and FTP operations
This dual-protocol compatibility ensures that no matter your toolset or tech stack, ProxyVault works right out of the box.
Built for SEO, Web Scraping, and Data Mining
Modern businesses rely heavily on data for strategy and operations. ProxyVault’s datacenter proxy API is custom-built for the most demanding use cases:
SEO Ranking and SERP Monitoring
For marketers and SEO professionals, tracking keyword rankings across different locations is critical. Our proxies support geo-targeting, allowing you to simulate searches from specific countries or cities.
Track competitor rankings
Monitor ad placements
Analyze local search visibility
The proxy API ensures automated scripts can run 24/7 without IP bans or CAPTCHAs interfering.
Web Scraping at Scale
From eCommerce sites to travel platforms, web scraping provides invaluable insights. Our rotating datacenter proxies change IPs dynamically, reducing the risk of detection.
Scrape millions of pages without throttling
Bypass rate limits with intelligent IP rotation
Automate large-scale data pulls securely
Data Mining for Enterprise Intelligence
Enterprises use data mining for trend analysis, market research, and customer insights. Our infrastructure supports long sessions, persistent connections, and high concurrency, making ProxyVault a preferred choice for advanced data extraction pipelines.
Advanced Features with Complete Control
ProxyVault offers a powerful suite of controls through its datacenter proxy API, putting you in command of your operations:
Unlimited bandwidth and no request limits
Country and city-level filtering
Sticky sessions for consistent identity
Real-time usage statistics and monitoring
Secure authentication using API tokens or IP whitelisting
These features ensure that your scraping or data-gathering processes are as precise as they are powerful.
Privacy-First, Log-Free Architecture
We take user privacy seriously. ProxyVault operates on a strict no-logs policy, ensuring that your requests are never stored or monitored. All communications are encrypted, and our servers are secured using industry best practices.
Zero tracking of API requests
Anonymity by design
GDPR and CCPA-compliant
This gives you the confidence to deploy large-scale operations without compromising your company’s or clients' data.
Enterprise-Level Support and Reliability
We understand that mission-critical projects demand not just great tools but also reliable support. ProxyVault offers:
24/7 technical support
Dedicated account managers for enterprise clients
Custom SLAs and deployment options
Whether you need integration help or technical advice, our experts are always on hand to assist.
Why Choose ProxyVault for Your Datacenter Proxy API Needs
Choosing the right proxy provider can be the difference between success and failure in data operations. ProxyVault delivers:
High-speed datacenter IPs optimized for web scraping and automation
Fully customizable proxy API with extensive documentation
No limitations on bandwidth, concurrent threads, or request volume
Granular location targeting for more accurate insights
Proactive support and security-first infrastructure
We’ve designed our datacenter proxy API to be robust, reliable, and scalable—ready to meet the needs of modern businesses across all industries.
Get Started with ProxyVault Today
If you’re ready to take your data operations to the next level, ProxyVault offers the most reliable and scalable datacenter proxy API on the market. Whether you're scraping, monitoring, mining, or optimizing, our solution ensures your work is fast, anonymous, and unrestricted.
Start your free trial today and experience the performance that ProxyVault delivers to thousands of users around the globe.
1 note
·
View note
Text
Proxy SwitchyOmega và cách sử dụng đơn giản | năm 2025
Proxy SwitchyOmega là gì?
Proxy SwitchyOmega là một tiện ích mở rộng (extension) dành cho trình duyệt Google Chrome và các trình duyệt dựa trên Chromium (như Microsoft Edge, Brave). Nó giúp người dùng dễ dàng quản lý và chuyển đổi giữa các cấu hình proxy khác nhau.

Chức năng của Proxy SwitchyOmega
Chuyển đổi proxy nhanh chóng: Cho phép bạn chuyển đổi giữa nhiều proxy khác nhau mà không cần vào cài đặt hệ thống.
Tạo nhiều cấu hình proxy: Hỗ trợ lưu trữ nhiều cấu hình proxy để sử dụng cho các mục đích khác nhau.
Tùy chỉnh quy tắc tự động: Bạn có thể thiết lập các quy tắc để tự động sử dụng proxy theo tên miền, URL hoặc IP cụ thể.
Kiểm soát lưu lượng mạng: Hỗ trợ theo dõi và kiểm tra kết nối để đảm bảo proxy hoạt động ổn định.
Hỗ trợ các giao thức proxy: Bao gồm HTTP, HTTPS, SOCKS4, SOCKS5.
Điểm nổi bật khi sử dụng Proxy SwitchyOmega
Chuyển đổi Proxy nhanh chóng: Chỉ cần một cú nhấp chuột để chuyển đổi giữa các cấu hình Proxy mà không cần vào cài đặt trình duyệt
Quy tắc tự động linh hoạt: Thiết lập quy tắc tự động để lựa chọn Proxy phù hợp dựa trên URL, IP hoặc tên miền. Điều này giúp tối ưu hóa trải nghiệm duyệt Web.
Quản lý nhiều cấu hình Proxy: Lưu trữ và quản lý nhiều cấu hình Proxy cùng lúc, tiện lợi khi cần chuyển đổi nhanh giữa các máy chủ Proxy từ các quốc gia khác nhau.
Hỗ trợ nhiều giao thức Proxy: Tương thích với HTTP, HTTPS, SOCKS4, SOCKS5, đáp ứng nhu cầu đa dạng của người dùng.
Không ảnh hưởng đến hiệu suất: Proxy SwitchyOmega hoạt động mượt mà, tiêu thụ ít tài nguyên, không làm chậm trình duyệt.
Miễn phí và không quảng cáo: Hoàn toàn miễn phí và không có quảng cáo, mang đến trải nghiệm người dùng tốt nhất.
Dễ dàng cài đặt và sử dụng: Giao diện thân thiện, dễ thao tác ngay cả với người mới bắt đầu.
Điểm hạn chế khi sử dụng Proxy SwitchyOmega
Chỉ hỗ trợ trình duyệt Chromium: Proxy SwitchyOmega chỉ hoạt động trên các trình duyệt dựa trên Chromium như Google Chrome, Microsoft Edge và Brave. Người dùng tiện ích Firefox hoặc Safari không thể sử dụng tiện ích này.
Không mã hóa dữ liệu: Proxy SwitchyOmega chỉ định tuyến lưu lượng qua Proxy mà không mã hóa dữ liệu.
Phụ thuộc vào Proxy có sẵn: Tiện ích không quá cung cấp Proxy mà chỉ giúp bạn quản lý Proxy có sẵn. Nếu không có Proxy chất lượng, trải nghiệm có thể bị ảnh hưởng.
Không ẩn địa chỉ IP toàn hệ thống: Khác với VPN, Proxy SwitchyOmega chỉ hoạt động trên trình duyệt, không ảnh hưởng đến các ứng dụng hoặc dịch vụ khác trên máy tính.
Không Bypass được một số Website: một số trang Web có hệ thống phát hiện và chặn Proxy, khiến việc sử dụng Proxy SwitchyOmega để vượt qua bị giới hạn.
Các bước cài đặt Proxy SwitchyOmega
Để có thể cài đặt nhanh chóng đối với Proxy SwitchyOmega xin mời các bạn cùng Clouding tiến hành theo các bước sau đây!
Bước 1: Truy cập vào tiện ích "Chrome" gõ từ khóa Proxy SwitchyOmega - Truy cập vào Link trình duyệt và tiến hành "Thêm vào Chrome"
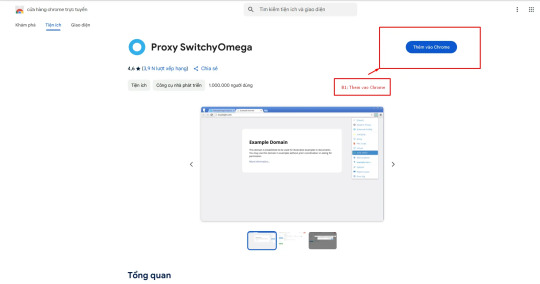
Bước 2: Tiến hành cài đặt Proxy cho tiện ích.
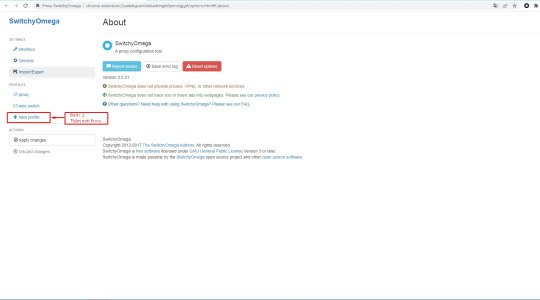
Bước 3: Điền thông tin chi tiết IP:Port:Usernam:Password và lưu thông tin.
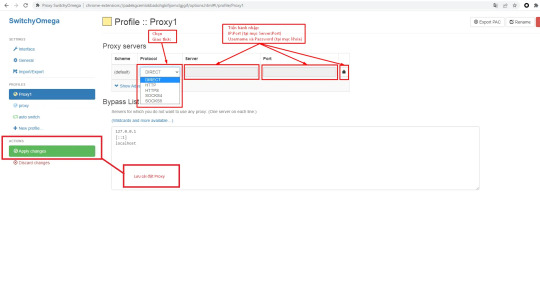
Bước 4: Hoàn thành và kiểm tra IP bằng cách truy cập vào Kiemtraip.vn xem IP gốc đã được thay đổi hay chưa, nếu đã thay đổi vậy là tiến hành thao tác thành công.
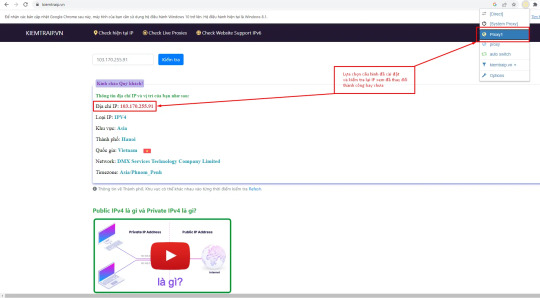
Khi đã cài đặt thành công thì có thể tiến hành triển khai ngay dịch vụ của các bạn!
Để có thể dễ dàng hơn trong việc cài đặt, Clouding đã cung cấp thêm cho các bạn video hướng dẫn cụ thể dưới đây để các bạn có thể cài đặt thành công trong lần cài đặt đầu tiên.
Video hướng dẫn: Hướng dẫn cài đặt Proxy SwitchyOmega //www.youtube.com/embed/yU8iHXl4kM0
Vậy làm thế nào để có thể tìm và mua được nguồn Proxy uy tín, độ bảo mật cao, chính hãng, đặc biệt đội ngũ support (kỹ thuật & tư vấn) cực kỳ nhiệt tình hỗ trợ 24/7. Xin mời các bạn cùng đến với Clouding.vn.
Mua Proxy chất lượng tại Clouding.vn
Clouding.vn là Website chuyên cung cấp VPS & Proxy chính hãng đa quốc gia. Gồm nhiều gói dịch vụ Datacenter lẫn các gói dịch vụ dân cư, hệ thống được xây dựng trên nền tảng công nghệ ảo hóa KVM tiên tiến, mang lại hiệu suất cao trong lĩnh vực điện toán đám mây.
Hy vọng rằng những thông tin trong bài viết đã giúp bạn có cái nhìn rõ hơn về tiện ích Proxy SwitchyOmega. Đừng ngần ngại liên hệ với Clouding nếu bạn có bất kỳ thắc mắc nào hoặc cần thêm sự tư vấn qua các phương thức liên lạc sau:
Số ĐT: 0888-662-393
Telegram: @cloudingvn
Zalo: 0888-662-393
Hoặc kênh chat trực tuyến trên Website nhé.
Hãy tiếp tục theo dõi Clouding để cập nhật thêm nhiều kiến thức hữu ích và mẹo hay mỗi ngày. Chúc bạn thành công và hẹn gặp lại các bạn trong những bài viết tiếp theo!
0 notes